Typical IT Data Center Security Precautions
- Thick concrete walls.
- Data, comms, and power redundancy.
- Mantrap entry control, CCTV and alarms.
- Stratified internal access controls.
- Locking server cabinets.
- Documented procedures.
- And, a SOC to knock your socks off.
But, what about…
- Electronic surveillance device detection.
- Wi-Fi security and compliance verification.
- Employee information policy compliance.
- Decaying security hardware discovery.
- Improper sensitive wastepaper disposal.
- Office equipment technology threats.
- Emerging information security threats.
These are the Achilles’ Heels of IT data centers.
The solution… Conduct periodic IT data center Technical Surveillance Countermeasures (TSCM) inspections.
Let’s look closer at a few of these information security loopholes.
Electronic Surveillance in IT Data Centers
Old fashioned bugs and wiretaps probably come to mind first. While they remain a threat, under appreciated items like cellular and Wi-Fi malicious USB cables and GSM bugs are favored by tech-savvy attackers. Miniature voice recorders and covert spy cameras are next on the list.
Finding these devices is the primary, but not the only, function of periodic IT data center TSCM inspections.
Wi-Fi Security & Compliance
Just one loophole…
Hackers are in.
Data is out.
&
“You are out of compliance.”
Wi-Fi is used by printers, VoIP phones, security cameras, and a variety of other IoT devices.
A common scenario… The IT department secures the Wi-Fi system when it is first installed. Then, an executive orders a printer from Amazon on their own. It comes with unsecured Wi-Fi turned on by default. Instant Achilles’ Heel. Hackers attack. Once this far in, they gain sensitive data, passwords, and can attempt further pivots into the network.
Competent IT data center TSCM inspections include Wi-Fi security and compliance audits.
General Information Security
 You probably have an information security policy. Does it include the proper storage of unattended sensitive paperwork, a clear desk policy, and the shredding of sensitive wastepaper? Are employees abiding by the policy? An IT data center TSCM inspection will identify and help you solve these issues.
You probably have an information security policy. Does it include the proper storage of unattended sensitive paperwork, a clear desk policy, and the shredding of sensitive wastepaper? Are employees abiding by the policy? An IT data center TSCM inspection will identify and help you solve these issues.
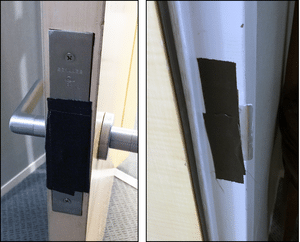
Security Hardware Fails
Security hardware may have been improperly installed, can break, decay in effectiveness, or be crippled on purpose, like this taped door lock. When the door was closed the compromise was invisible. IT data center TSCM inspections uncover security hardware fails like these.
Office Technology Threats
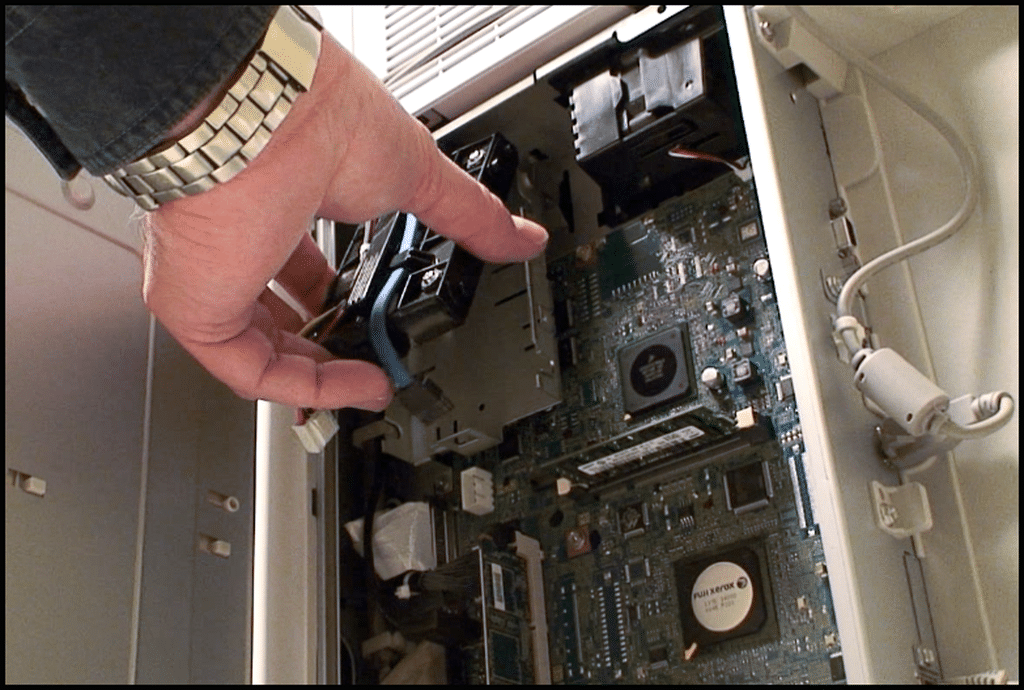
Advanced office equipment can be very helpful. Networked print centers are a good example. Their Achilles’ Heel, however, is that all print jobs are stored into memory and can be remotely extracted, or have their hard drive swapped out. IT data center TSCM inspections will alert you to office security vulnerabilities, and offer solutions.
If you have any questions, or would like to schedule an IT data center TSCM inspection, just let us know.
###
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.
EXTRAS:
• More security tips, spy and privacy news at spybusters.blogspot.com. Be sure to sign up for the free email updates.
• Concerned about Spy Cameras? Learn how to detect them.


 Just one loophole…
Just one loophole…