(VIDEO) (Detection Instructions)
The Background of Malicious USB Cables
A malicious cable is any cable (electrical or optical) which performs an unexpected, and unwanted function. The most common malicious capabilities are found in USB cables. Data exfiltration, GPS tracking, and audio eavesdropping are the primary malicious functions.
The first malicious USB cables began life as an NSA-created spy tool under the code name COTTONMOUTH in 2008. The government paid a lot for it. The cost for their spy cable back then was $1,015.00, in quantities of 50. Now, they are a fraction of that cost on various websites across the internet. Fast Company reports it, “should send shivers through everyone in the privacy and security.”
Malicious USB Cable Capabilities
 The general expectation is that a cable performs no other function than to transfer energy and/or information (electrically or optically) between two points. Malicious USB cables do much more.
The general expectation is that a cable performs no other function than to transfer energy and/or information (electrically or optically) between two points. Malicious USB cables do much more.
- Some act as eavesdropping bugs which can automatically record calls. Or, call a pre-programmed phone number, whenever voices are heard. They draw their power from whatever they are plugged into, and use the cellular phone system to make the call.
- Some also have GPS tracking capability; perfect for vehicle surveillance.
- The worst malicious cables take control of a user’s cell phone, laptop, or desktop. User names and passwords are the first bits to go. Next, the connected device’s storage is emptied. Next, pre-loaded penetration tools spring into action. The connection is used as a pivot point to attack other machines and databases on the network. All of this is controlled remotely by an outside hacker, via Wi-Fi to the internet, or nearby smartphone. The hacker roams unnoticed on the network, motives unknown.
Once the hacker has infiltrated the network, more data can be extracted, viruses planted, or a ransomware attack staged. This is dangerous in a business environment.
All this from an innocent-looking USB cable!
Malicious USB Cable Threat Assessment
-
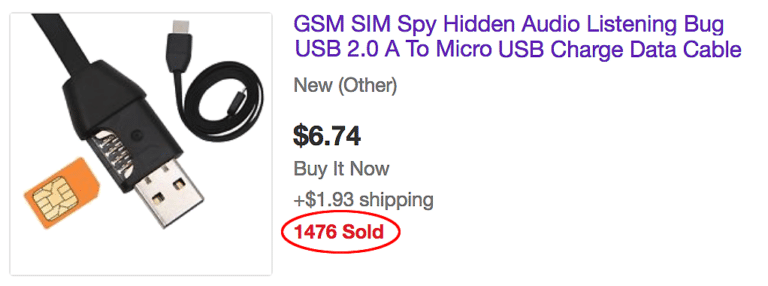
 Most look exactly like regular USB cables.
Most look exactly like regular USB cables.- They are openly sold on the internet.
- Costs range from $6.74 to $119.99.
- Placement in an office environment is easy.
- Once in place they won’t be suspected.
- Discovery is impossible without inspection.

Sometimes these “value added” cables are sold as legitimate penetration testing tools. Unfortunately, sales are not restricted to just legitimate cybersecurity practitioners. Other times they are openly advertised as spy cables.
Detecting Malicious USB Cables
In light of today’s serious ransomware attacks and corporate espionage attacks, businesses need a way to inspect for this threat.
- Murray Associates researched the problem.
- We purchased and tested several malicious USB cables. From what was learned during these tests our technical staff developed several new inspection protocols.
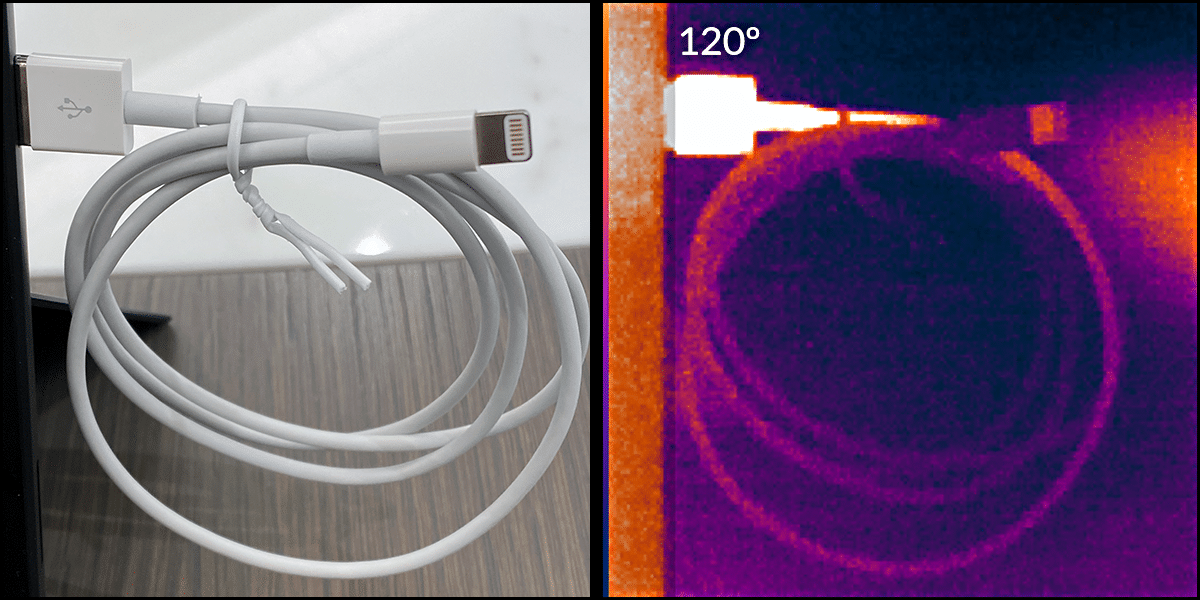
- One of our inspection methods uses an infrared camera to detect heat. As shown on the right, the heat given off by an active malicious USB cable can be easily seen using this detection technique.
TIP: You might be able to tell just by touching the cable head. If it feel slightly warm, suspect the worst, and give us a call.
- Cables plugged into devices which are turned off, or are just laying around, require our alternate test procedures.
TIP: Treat USB cables like a toothbrush. You wouldn’t use one you found laying around, would you? - The testing procedures we developed have been added to our Technical Surveillance Countermeasures (TSCM) inspection process. Once a cable has been vetted as legitimate it is marked with a small security sticker.
TIP: Whenever you get a new USB cable from a manufacturer you trust, place an inconspicuous ink mark or scratch on it. That way you will know if it has been replaced with a malicious spy cable. - Upon completion of a TSCM evaluation we teach our clients how to quickly vet new USB cables entering their environments in between our visits. We also provide them with a testing device.
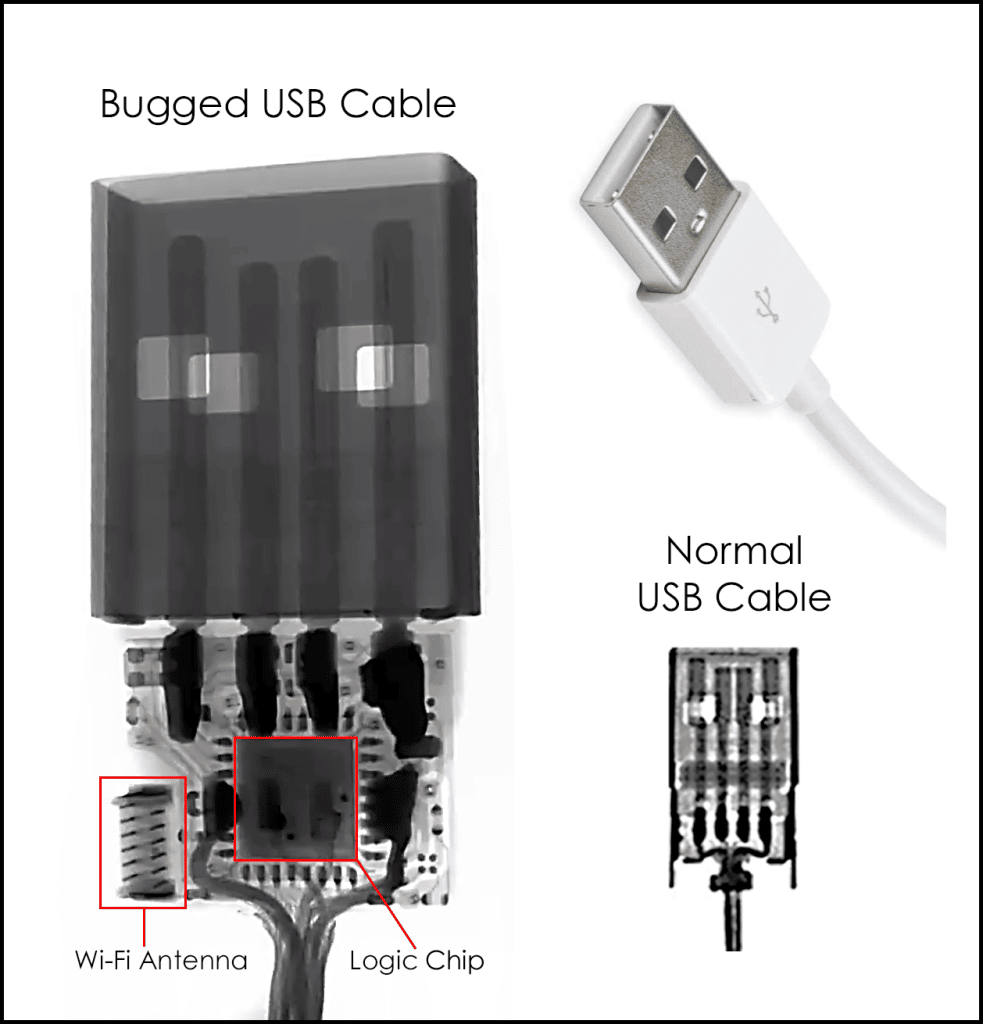 Note: Malicious USB cables do not have to be attached to anything other than an active USB port. These do their dirty work by extracting data or taking control of the device. Other spy cables which are only connected to a power plug or jack act as eavesdropping and GPS trackers.
Note: Malicious USB cables do not have to be attached to anything other than an active USB port. These do their dirty work by extracting data or taking control of the device. Other spy cables which are only connected to a power plug or jack act as eavesdropping and GPS trackers.
 Can you identify the bugged cable?
Can you identify the bugged cable?
No worries. You can’t tell just by looking, even we can’t.
That’s why we put a small black mark on it.
It is Cable 3.
——
In case you are interested in actually seeing malicious USB cables for sale, here are a few links… 1, 2, 3, 4, 5
Malicious USB Cables: Frequently Asked Questions
- What Is an Evil USB? Evil USB cable is another commonly used term for a malicious USB cable. Essentially, it’s a USB that’s been compromised by an external party and can listen in on conversations, export data, and receive commands from nearby smartphones. If an evil USB cable finds its way into your business, then it can be a huge threat to your security.
- Can a USB Cable Hack Your Phone? Yes, a malicious USB cable can hack your phone. The compromised cable can be controlled remotely by a hacker and used to steal your data, and even take control of the device.
- Can a USB Cable Be Infected with a Virus? A malicious USB cable won’t contain a virus, but it will allow hackers access to your device and they can introduce a virus that way. Essentially, it gives free rein over your device to an outside party.
- What Is Bad About a USB Cable? There’s nothing bad about a USB cable, in fact, they’re extremely useful and that are used for many day-to-day tasks. Like with anything though, they can be compromised, and in the case of malicious USB cables, they can completely compromise your security.
- Can a USB Cable Be Hacked? As malicious USB cables show, USB connections can be hacked. Most commonly though, your USB cable is most likely to be hacked when it is replaced without your knowledge, rather than somebody tampering with an existing USB cable. This is why we recommend you put an identifiable mark on USB cables you buy directly from the manufacturer, so you know they’ve not been switched with a malicious USB cable.
###
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.
EXTRAS:
• More security tips, spy and privacy news at spybusters.blogspot.com. Be sure to sign up for the free email updates.
• Concerned about Spy Cameras? Learn how to detect them.


 Most look exactly like regular USB cables.
Most look exactly like regular USB cables.