Executive Summary
24/7 Radio Transmission Monitoring (RTM) systems are being marketed as a “Continuous TSCM” solution. The implication is misleading. 24/7 RTM may be an addition to on-site TSCM audits, but it is not a replacement. Security is reduced and risks increase when RTM is employed to replace, or dilute, a strong holistic TSCM program. This paper explains why.
Continuous TSCM RTM Marketing Statements Evaluated
- “The basic Enterprise set up provides real-time visibility and situational awareness into the Big 4 protocols operating in your facility: Cellular, Bluetooth, Bluetooth Low Energy, and Wi-Fi.” “…any device emitting cellular, Wi-Fi, Bluetooth or BLE.“
Reality: The primary focus of RTM systems is on the most obvious types of “radio-frequency” transmitters; ones which broadcast unique identifying information. Not detected at all are the other transmitters described in the Limitations section below. Intelligence collection professionals know this and will employ alternate espionage techniques and technologies.
- “…sensor arrays detect wireless emitter activity from 25 MHz to 6 GHz.”
Reality: Be aware, a majority of frequency space is not monitored by RTM Continuous TSCM sensor arrays. Professional TSCM teams routinely analyze the frequency spectrum from .009 MHZ to 24 GHz; over three times the territory!
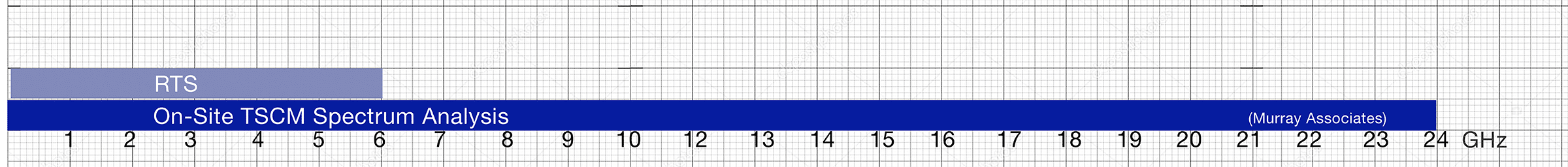 This is important. Example… 10 GHz bugs have been available since 1992. (source) This type of eavesdropping device, and other devices which transmit outside the RTM’s limited reception range (25 MHz to 6 GHz), will only be detected during an on-site TSCM inspection. Again, intelligence collection professionals know the limitations of RTM systems and will work around them.
This is important. Example… 10 GHz bugs have been available since 1992. (source) This type of eavesdropping device, and other devices which transmit outside the RTM’s limited reception range (25 MHz to 6 GHz), will only be detected during an on-site TSCM inspection. Again, intelligence collection professionals know the limitations of RTM systems and will work around them.
- “Devices that violate location policy and are managed by MDM or UEM, can be automatically turned off or otherwise disabled using rules…”
Reality: MDM (Mobile Device Management) controls only keep honest people honest. Controls can be bypassed (and reinstated) in seconds by the owner of the communications device. (source) Thus, exfiltration may be too quick to stop, or worse, go unnoticed. Also, device owners must accept placement of MDM control software on their devices; not a requirement which can be practically applied to all visitors.
Serious Limitations
Continious TSCM Radio Transmission Monitoring hardware will NOT…
- Detect miniature voice recorders.
- Detect covert spy cameras which record to SD cards instead of transmitting.
- Detect bugs in the .009 MHz—25 MHz and 6 GHz—24 GHz frequency ranges.
- Detect bugs which transmit over power lines or other direct wiring paths.
- Detect bugs which use light waves for transmission.
- Detect acoustical leakage which can facilitate eavesdropping.
- Detect external visual surveillance vulnerabilities.
(Computer screen and personnel surveillance.) - Detect employee compliance with corporate information security policies.
(Key control, sensitive wastepaper disposal, etc.) - Detect vulnerabilities introduced by new office technologies.
- Detect access control hardware decay and operational failures.
(Easily bypassed door locks and Request-to-Exit sensors, for example.) - Report emerging security threats, technical, hacking and otherwise.
- Report safety related observations. (Fire hazards, water leaks, etc.)
- Report on directly observed information security vulnerabilities.
- Provide independent recommendations for security enhancements.
- Provide independent technical security device evaluations.
- Provide evidence required to legally protect trade secrets in court.
TSCM technical specialists, providing on-site audits, do all of the above.
Other “Continious TSCM” Issues to Consider
Marketing Statement #4: “Data will help accelerate compliance audits of your facility and detect unauthorized wireless devices before (?!?) they enter your secure space.”
- Who actually monitors the RTM sensor system 24/7?
- What is report & response time if an issue arrises? Will it be quick enough?
- Who responds?
- Will the responder know what to look for, and how to handle a find?
- What is the false alarm rate?
- Can a radio-frequency emission on an adjacent floor trigger an alert?
- Will the system be tested periodically by an independent specialist?
Recommendations
- If considering adoption of any Continuous TSCM RTM system, do so on a limited basis initially.
- Evaluate its effectiveness. See what issues surface.
- Continue scheduled, holistic, on-site TSCM audits.
- Feel free to contact us with any questions, or for additional information.
###
Kevin D. Murray CPP, CISM, CFE, CDPSE is a counterespionage consultant and TSCM specialist with over four decades of experience.
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.




