(PDF version) (VIDEO)

These are the key measurements for identifying malicious spy cables.
Measurements for a legitimate USB cable.
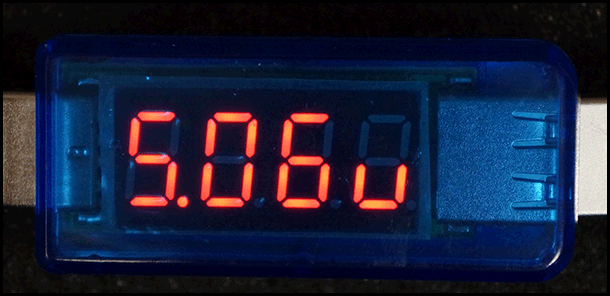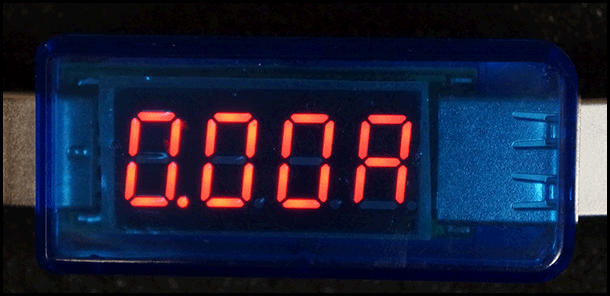
Measurements for a malicious spy cable.

The Murray Associates USB Spy Cable Detector is simple and easy to use.

SPY CABLE DETECTOR INSTRUCTIONS:
- Plug the detector into an active USB port (An outlet charging cube, laptop, or desktop computer, for example.)
- The readings on the detector will alternate between voltage and current. Voltage and current are indicated on the right side of the digits. The voltage indicator looks like a small “u”. Current, measured in Amps, is indicated with a flat top “A”.
- You should see readings close to 5.05 Volts and exactly 0.00 Amps without anything plugged into the detector. This is normal.
- Plug the cable you are testing into the other end of the detector. If the readings do not change, the cable is normal.
- An abnormal, or malicious spy USB cable, may show a change in voltage, but not always. What will change is the current (measured in Amps). Malicious USB spy cables show readings in the range of 0.02 to 0.05 Amps.
- If you come across a malicious USB spy cable follow the instructions below, and contact us for deeper testing of the cable, and further investigative assistance. There is more to the attack on your privacy than just one spy cable.
Detectors kits are given to our clients at no charge. They use them to inspect new USB cables coming into their environments in between our scheduled inspections. The Data Spy Blocker prevents data siphoning while using public charging station.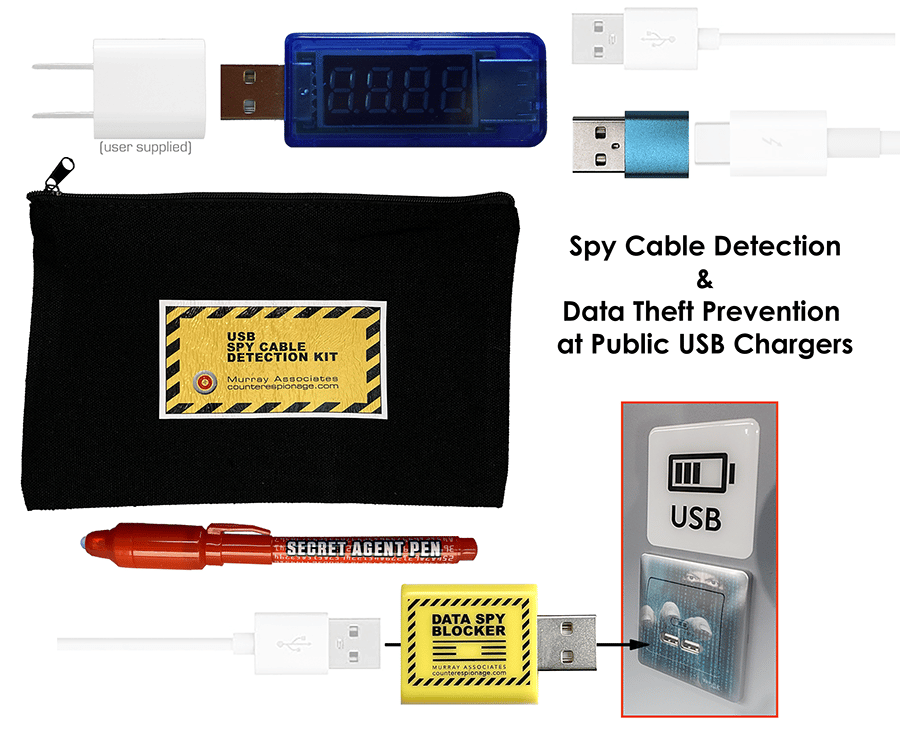
The “I think I found a bug” procedural checklist:
- Do not disturb the device. It is evidence.
- Do not alert the eavesdropper by talking.
- Secure the area. It is a crime scene. (Use a non-alerting excuse.)
- Document your evidence. Make notes. Take photos.
- Notify only people who have a real need-to-know.
- Tell all persons involved to keep it confidential.
- Contact an independent information security consultant who specializes in Technical Surveillance Countermeasures (TSCM).
- Make you call from a safe area, using a safe phone, of course.
Your Technical Surveillance Countermeasures specialist will work with you to:
- complete the documentation process;
- inspect for additional, or supplementary devices;
- evaluate the situation; answer your questions;
- make suggestions as to how to identify the eavesdropper;
- and help you develop an information protection strategy for the future.
###
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.
EXTRAS:
• More security tips, spy and privacy news at spybusters.blogspot.com. Be sure to sign up for the free email updates.
• Concerned about Spy Cameras? Learn how to detect hidden cameras.