Home » About Murray Associates » History of Innovations
• Murray Associates was the first TSCM firm with a published Operating Policy, and fixed Fee and Expense Schedule. Before this, practitioners either charged using unpredictable hourly fees, or flat-rates based on how much they thought they could charge. Some still do.
• We were also the first TSCM firm with a polygraph policy, to combat the “plant a bug, grow more work” mentality which was rampant at the time. Upon our discovery of bugging, wiretapping, or other forms of eavesdropping, clients have always had the right to verify our findings.
 The US Government lifted secrecy and sales restrictions on the MicroLab/FXR Non Linear Junction Detector. Murray Associates was the first in the private sector to utilize this unusual instrument which detected bugs even if they were “off” or had dead batteries!
The US Government lifted secrecy and sales restrictions on the MicroLab/FXR Non Linear Junction Detector. Murray Associates was the first in the private sector to utilize this unusual instrument which detected bugs even if they were “off” or had dead batteries!
Miniature television cameras with AM micro-transmitters (900 MHz frequency range) became a major threat. Murray Associates was the first countermeasures firm to purchase a spectrum analyzer (Tektronix 2710) capable of receiving and viewing these TV signals.

 Laser beam eavesdropping captures the media’s attention and cause our clients concern. In order to accurately assess the threat, Murray Associates built a laser beam eavesdropper. Our findings were very informative and put the threat into realistic perspective.
Laser beam eavesdropping captures the media’s attention and cause our clients concern. In order to accurately assess the threat, Murray Associates built a laser beam eavesdropper. Our findings were very informative and put the threat into realistic perspective.
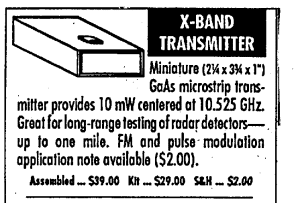 We discover a small company selling 10 GHz transmitter kits for $29. Incredibly, the plans for adding FM audio capabilities and turning it into a bug cost only $2 more. Inspection of radio frequencies above 1.8 GHz was rare at the time. We immediately boosted our audit capabilities and alerted our clients.
We discover a small company selling 10 GHz transmitter kits for $29. Incredibly, the plans for adding FM audio capabilities and turning it into a bug cost only $2 more. Inspection of radio frequencies above 1.8 GHz was rare at the time. We immediately boosted our audit capabilities and alerted our clients.
 Miniature television cameras with FM microtransmitters (2.4 GHz frequency range) become a major threat. Most “countermeasures” equipment at the time couldn’t see these signals. Drawing together various technologies, Murray Associates created a system that was the next step in the evolution of spectrum analysis – Radio-Reconnaissance Spectrum Analysis™.
Miniature television cameras with FM microtransmitters (2.4 GHz frequency range) become a major threat. Most “countermeasures” equipment at the time couldn’t see these signals. Drawing together various technologies, Murray Associates created a system that was the next step in the evolution of spectrum analysis – Radio-Reconnaissance Spectrum Analysis™.
New digital telephone systems are vulnerable to digital wiretaps and feature manipulation. Murray Associates develops a FFT technique to help detect these problems. Also in 1999, Spybusters.com the initial Murray Associates website becomes the first Internet site to honor eavesdropping history makers.
 We begin experimenting with infrared thermal imaging technology in 1999. After a year of research, we purchased a $60,000.00 thermal imager and the Thermal Emissions Spectrum Analysis™ (TESA™) inspection technique is born.
We begin experimenting with infrared thermal imaging technology in 1999. After a year of research, we purchased a $60,000.00 thermal imager and the Thermal Emissions Spectrum Analysis™ (TESA™) inspection technique is born.
Wireless Local Area Networks become popular in many corporations and executive homes. So does inserting rogue wireless nodes into supposedly secure hard-wired systems. The threat… wireless wiretapping. Appropriate detection instrumentation is brought on board.
VoIP telephony becomes the rage, offering more affordable calls. While irresistible to clients, these services were vulnerable to wiretapping, denial of service attacks, and theft of services. Murray Associates was the first in our field to research this communications “advancement,” and provide our clients with a safe migration strategy.
At our clients’ request, Murray Associates established a local presence in the European Union and Oceania/Australasia.
 Sony releases the first price-practical ($6,000.) UV digital television camera. We experiment with bringing this major technical advancement into our field. Evidence of electronic eavesdropping installations are viewed and documented with reflected and absorbed ultraviolet light.
Sony releases the first price-practical ($6,000.) UV digital television camera. We experiment with bringing this major technical advancement into our field. Evidence of electronic eavesdropping installations are viewed and documented with reflected and absorbed ultraviolet light.
Continuing research into new sensing instrumentation, we invested approximately $40,000.00 in government-level new NLJD instrumentation for our clients. One of the most exciting capabilities of the new equipment is their ability to “hear” video cameras hidden within objects like clocks, radios, furniture, ceilings, etc.

 We are the first in the private sector to invest ($109,000.00) in Real-Time Spectrum Analysis with DPX technology for our clients. DPX makes previously invisible bug signals visible.
We are the first in the private sector to invest ($109,000.00) in Real-Time Spectrum Analysis with DPX technology for our clients. DPX makes previously invisible bug signals visible.
 A new Multifunction Digital Telephone Analyzer, with VoIP capabilities, became available. We immediately upgraded, at a cost of $19,000.00. It combined the functions of multiple instruments into one unit. This made room for additional instrumentation in our kit and allowed the detection of digital voice leaks on phone lines.
A new Multifunction Digital Telephone Analyzer, with VoIP capabilities, became available. We immediately upgraded, at a cost of $19,000.00. It combined the functions of multiple instruments into one unit. This made room for additional instrumentation in our kit and allowed the detection of digital voice leaks on phone lines.
 GSM bugs began flooding the Internet ‘spy shops’ and eBay for as little as $25.00. They are very difficult to locate as they are dormant when not actively being listened to. In response to client’s concerns, Murray Associates developed Digital Surveillance Location Analysis™ (DSLA™) using modified instrumentation from AirPatrol Corporation.
GSM bugs began flooding the Internet ‘spy shops’ and eBay for as little as $25.00. They are very difficult to locate as they are dormant when not actively being listened to. In response to client’s concerns, Murray Associates developed Digital Surveillance Location Analysis™ (DSLA™) using modified instrumentation from AirPatrol Corporation.
Spyware on “smart” cell phones hit critical mass this year. Clients and website visitors asked for a solution. What began as an executive briefing turned into a book – “Is My Cell Phone Bugged?: Everything You Need to Know to Keep Your Mobile Conversations Private” is released in early 2011.
 • Our travel kit inspection capabilities were upgraded with the acquisition of a 50 kHz to 24 GHz spectrum analyzer.
• Our travel kit inspection capabilities were upgraded with the acquisition of a 50 kHz to 24 GHz spectrum analyzer.
• Murray Associates staff completed a law enforcement oriented cell phone forensics training course. The instructor was the Chief Detective in charge of the Pennsylvania State Police Digital Forensics Lab at the time.
• “Is My Cell Phone Bugged?: Everything You Need to Know to Keep Your Mobile Conversations Private” was officially released June 1st. It received excellent reviews at amazon.com, and now has its own web site.
• Development of a Closed Country Information Security Protocol for our clients.
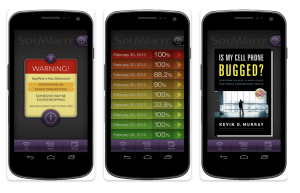 Is My Cell Phone Bugged?: Everything You Need to Know to Keep Your Mobile Conversations Private – becomes a spyware evaluation app for Android smartphones. SpyWarn 2.0 is available at Google Play.
Is My Cell Phone Bugged?: Everything You Need to Know to Keep Your Mobile Conversations Private – becomes a spyware evaluation app for Android smartphones. SpyWarn 2.0 is available at Google Play.
Electronic components continue to get smaller and standard non-linear junction detection was not keeping pace. When new technology became available, we were the first to offer its use to the private sector in the U.S.

 • SpyWarn™ 2.0 the forensic spyware evaluation app for Android is publicly launched on Google Play.
• SpyWarn™ 2.0 the forensic spyware evaluation app for Android is publicly launched on Google Play.
• This is quickly followed by the SpyWarn™ Anti-Spyware Kit for Smartphones. This security hardware is exclusively available to Murray Associates clients, free of charge.
• Bugging becomes a concern at cryptocurrency offices and data centers. We developed specialized TSCM procedures for our clients.
 Video voyeurism using covert spycams has become a serious problem. It is affecting individuals and organizations alike. At the request of one of their Fortune 100 clients, Murray Associates created a Spycam Detection training course. The course provides the security training necessary to detect video voyeurism at any location where there is an expectation of privacy. It is also available to businesses and individuals at Udemy.com as a self-paced, instructional video training course.
Video voyeurism using covert spycams has become a serious problem. It is affecting individuals and organizations alike. At the request of one of their Fortune 100 clients, Murray Associates created a Spycam Detection training course. The course provides the security training necessary to detect video voyeurism at any location where there is an expectation of privacy. It is also available to businesses and individuals at Udemy.com as a self-paced, instructional video training course.
 We introduced 360º degree photographic documentation of the sensitive areas we inspect as part of our electronic surveillance detection (TSCM) protocol. This assures we will detect subtle changes or additions during re-inspections. (Photo – Inspection of limousine wheel well.)
We introduced 360º degree photographic documentation of the sensitive areas we inspect as part of our electronic surveillance detection (TSCM) protocol. This assures we will detect subtle changes or additions during re-inspections. (Photo – Inspection of limousine wheel well.)
Our client asked us to manage eight TSCM inspections… all at different locations (some international), same day, same time, and repeated every week for three weeks. Our excellent network of associates handled it flawlessly.
A new technology, Backscatter X-ray, is being deployed by U.S. Customs as a drug and money detection aid. We field tested this instrument to see if we could use it to help our clients. As amazing as the technology is, we found the screen resolution needed improvement for our purposes. We will keep our eye on it.
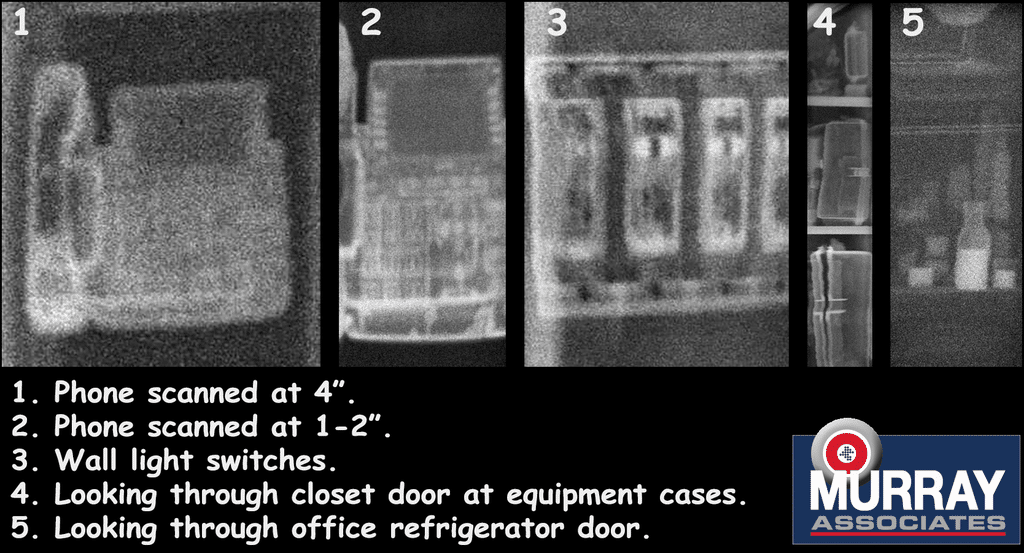
We conducted a full, hands-on analysis of the new, computer-assisted X-ray, for possible TSCM detection use. It is very effective and visually interesting. However, we found our already advanced TSCM instrumentation detects eavesdropping devices equally well, without using radiation.

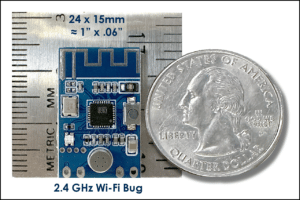 We discovered a new type of bug. It transmits via Wi-Fi and costs less than $10. We built one for testing and found it is undetectable using normal Wi-Fi analysis tools. We also figured out how to detect it.
We discovered a new type of bug. It transmits via Wi-Fi and costs less than $10. We built one for testing and found it is undetectable using normal Wi-Fi analysis tools. We also figured out how to detect it.
 • New types of Wi-Fi and Bluetooth instrumentation were added to our detection capabilities.
• New types of Wi-Fi and Bluetooth instrumentation were added to our detection capabilities.
• We evaluated new technologies to discover their eavesdropping potentials (Bluetooth stethoscope and Flipper Zero). The result, we developed new detection insights and protocols, now part of our inspection process.
 • Acquired the COMET RGB Camera Lens Detector, to enhance our covert camera detection protocol. This instrumentation is specifically designed to detect concealed and embedded cameras.
• Acquired the COMET RGB Camera Lens Detector, to enhance our covert camera detection protocol. This instrumentation is specifically designed to detect concealed and embedded cameras.
• Published: The Security Director’s Guide to Planning an Effective TSCM Sweep. A free download for the business community to help them curb corporate espionage.
• TSCM wiki created. Counterespionage.com becomes the first site of its kind to be AI powered.

• Ultrasonic acoustic camera added to our inspection protocol. Fast detection and pinpoint location of ultrasonic eavesdropping and infrasonic harassment devices. A major technological advancement.
• New Book: Corporate Espionage 101: The Missing Business School Course “Everything you need to know to counter the most common business and personal spy tactics” is in the editing stage. To be published in 2026.
• Evaluated multiple low-cost consumer spy camera detectors for our clients’ corporate travelers. A few are highly recommended!
We are working on it right now!


 Radio-frequency spectrum analysis technology advanced, and we kept pace. Three new Real-Time,
Radio-frequency spectrum analysis technology advanced, and we kept pace. Three new Real-Time, 