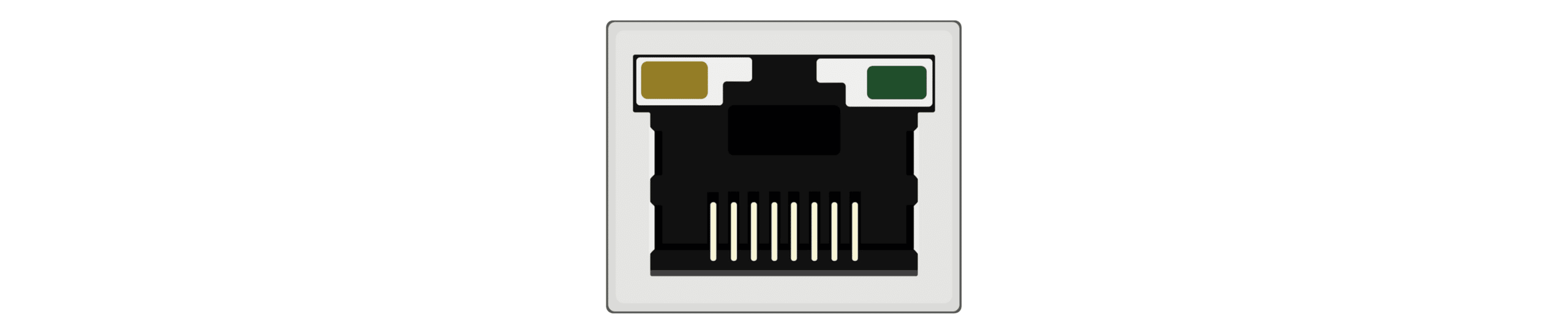
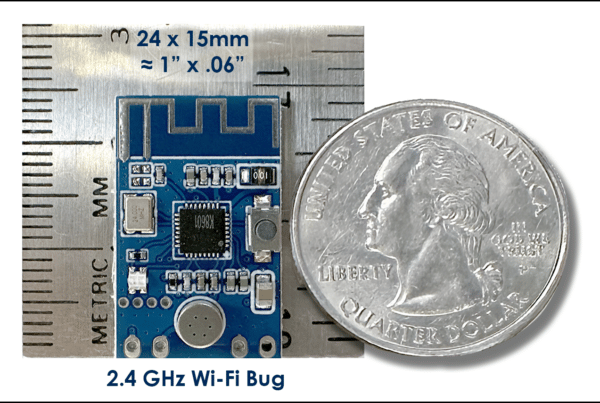
When inspecting IT / MDF / IDF rooms for unauthorized equipment and connections be sure to include a visual inspection of the router switches. While not a definitive evaluation, visual indicators are important first clues. Example…
 Currently, one of the most popular switches one is likely to encounter is the Cisco 2960.
Currently, one of the most popular switches one is likely to encounter is the Cisco 2960.
Spotting Counterfeit IT Gear
“The suspected counterfeit switch (left) has port numbers in bright white, while the known genuine device has them in grey. The text itself is misaligned. The triangles indicating different ports are different shapes.” (F-Secure)
Additionally, note the thickness of the top gray bars and the shade differences of the yellow. Fonts, text alignment and color shades are the prominent external indicators of fake or counterfeit items in general. Once sensitized to this, spotting fakes becomes much more easy. A YouTube video about fake calipers provides an excellent educational start.
In this photo note, “The mode button’s shape is slightly different. The square next to the management port is greenish on the counterfeit switch. On the genuine device, it is bright yellow.” 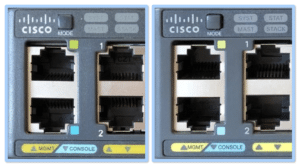
Internal inspection is another way to spot counterfeit IT gear. It reveals more clues, such as: missing authentication stickers, sloppy assembly, integrated circuits without identification markings, and “extra” components—possibly spy related—soldered onto the circuit board.
As always, if you see something, say something. (pdf version)
###
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.