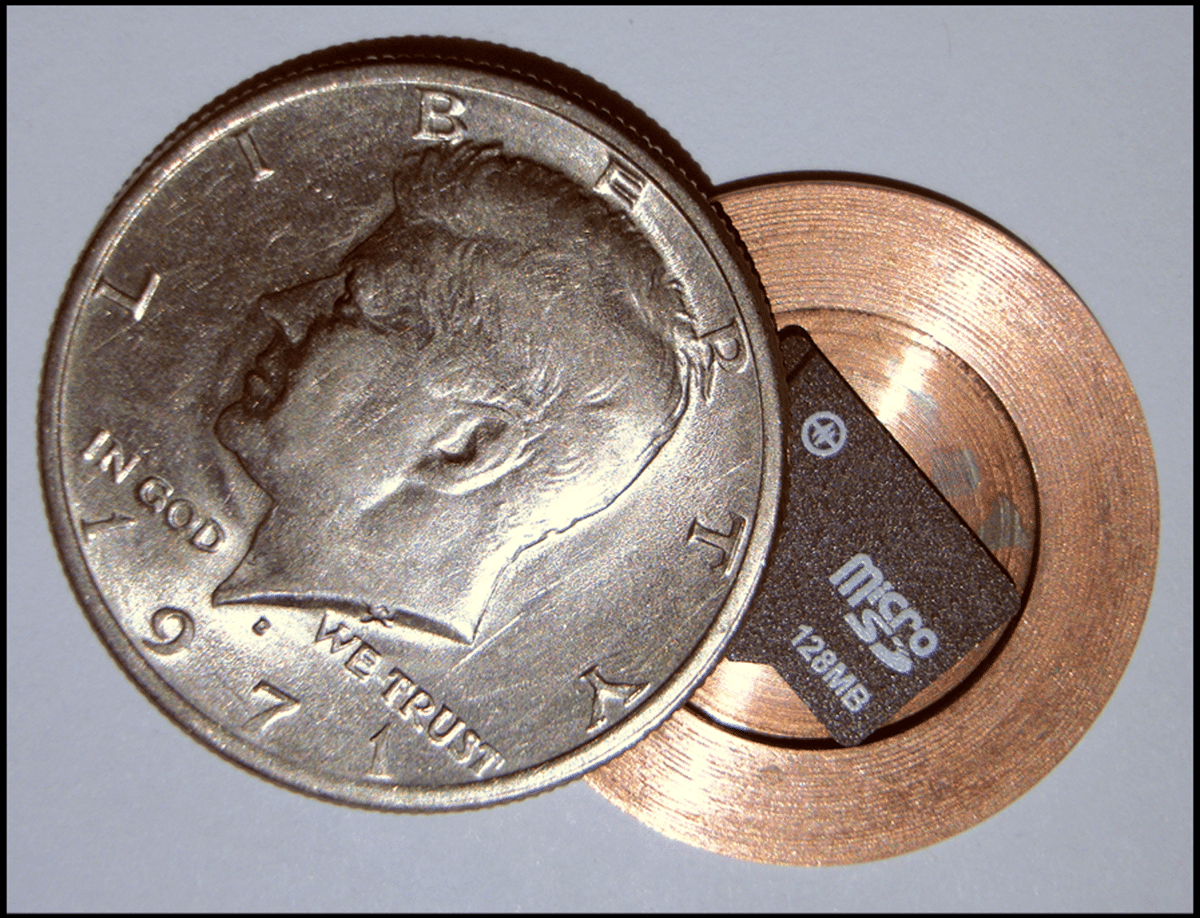
Protecting your business from corporate espionage spy techniques starts with knowing where to look. However, many businesses never look. Understandable. They are too busy running their businesses. And, corporate espionage spy detection was never taught in business school. Catch up now…
Murray Associates list of the Top 20 Corporate Espionage Spy Techniques
- Social engineering: Spies may use techniques to manipulate people into providing sensitive information or access to systems, such as phishing emails, pretexting, or impersonation.
- Physical access: Spies may try to gain physical access to a company’s premises to gather information through means such as tailgating, stealing badges, or planting listening devices.
- Dumpster diving: Spies may rummage through a company’s trash to find confidential information such as documents, reports, or electronic devices.
- Hacking: Spies may attempt to breach a company’s computer systems or networks to access sensitive data.
- Shoulder surfing: Spies may watch over the shoulder of an employee while they work on their computer or mobile device to observe confidential information.
- Wiretapping: Spies may intercept telephone conversations, voicemail messages, or other electronic communications to gather information.
- Covert surveillance: Spies may use cameras, bugs, or other surveillance techniques to monitor company activities or personnel.
- Blackmail: Spies may use threats or coercion to force employees to provide access to confidential information.
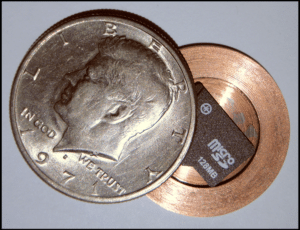
- Insider threats: Spies may target employees who have access to sensitive information and attempt to bribe or recruit them to share confidential information.
- Social media: Spies may use social media platforms to gather information about a company’s employees, operations, or business partners.
- Business travel: Spies may try to gather information by monitoring company travel itineraries, booking hotels near the target company, or impersonating business partners.
- Impersonation: Spies may impersonate a company employee or representative to gain access to sensitive information or assets.
- Third-party vendors: Spies may target third-party vendors who have access to a company’s systems or data.
- Physical surveillance: Spies may use physical surveillance techniques to gather information, such as following employees, observing meetings, or taking photos or videos.
- False job applications: Spies may submit false job applications to a company to gain access to sensitive information or to network with employees.
- Social events: Spies may attend company social events or conferences to gather information about employees or business partners.
- Eavesdropping: Spies may listen in on conversations between employees or business partners to gather information.
- Supply chain attacks: Spies may target a company’s suppliers or vendors to gain access to sensitive information or to introduce malware into a company’s systems.
- Remote access: Spies may attempt to gain remote access to a company’s systems or data through methods such as phishing or malware.
- Physical theft: Spies may steal physical assets such as laptops, mobile devices, or hard drives that contain sensitive information.
The list of corporate espionage spy techniques can be overwhelming. A Technical Surveillance Countermeasures (TSCM) information security consultant can help you reduce the risk. Here’s how to select a competent TSCM consultant to help you.
###
Murray Associates is an independent technical information security consulting firm. They provide electronic surveillance detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.