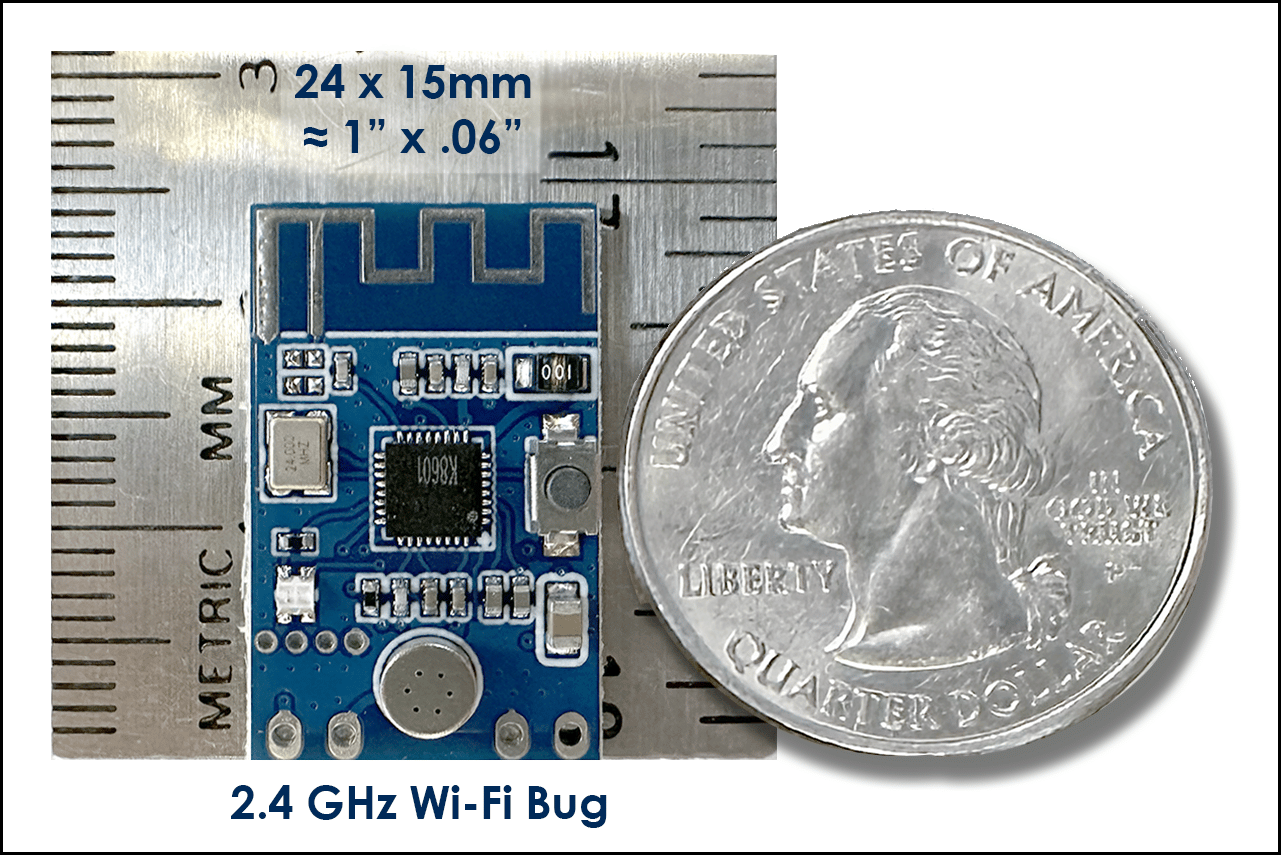
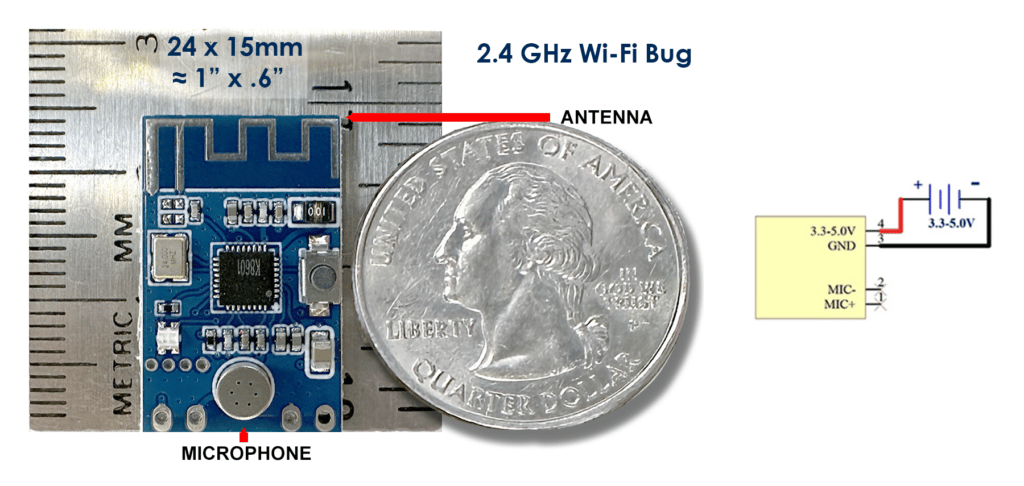
This 2.4 GHz bug is just one of many eavesdropping devices, GPS trackers and spy cameras flooding the market these days. Corporations that value information security and privacy need to be especially alert.
These surveillance devices may not be sophisticated, but they are very effective. Worse, they are readily available to anyone with a credit card and an internet connection. Most are so inexpensive they are considered “toss-away” — use once, don’t retrieve — perfect for short-term, low-risk use.
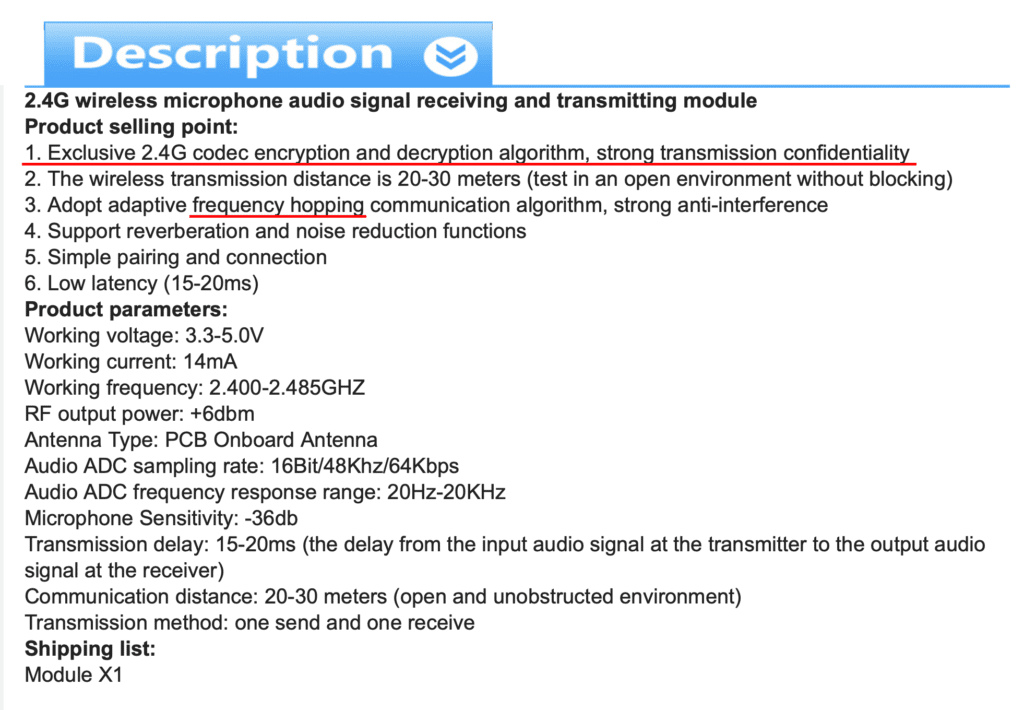
Let’s examine the 2.4 GHz bug ad…
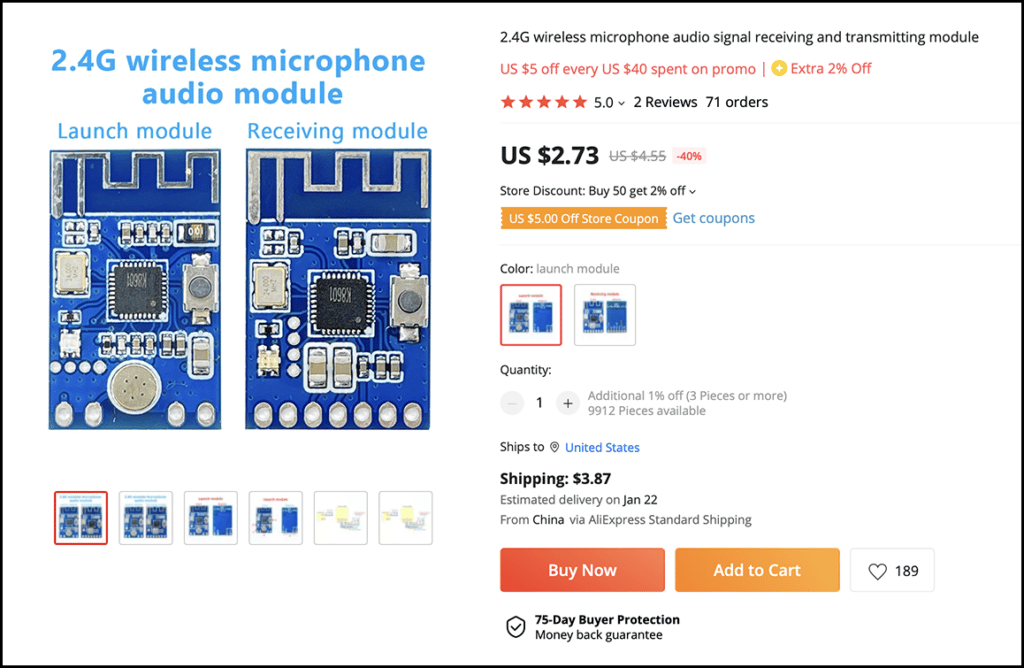
It comes semi-assembled. Total cost for one transmitter, one receiver, plus shipping: $9.33. Just add batteries and an audio amplifier on the receiving side, and you now have a spread-spectrum, encrypted, Wi-Fi bug. Here is how the seller describes their product…
A few years ago, this would have been considered science fiction or a very expensive government surveillance gadget. Today, it is the price of a Venti Latte and a breakfast sandwich.
2.4 GHz bugs are very small. They can be hidden anywhere, or built into anything. The power supply or battery will be the biggest component. Consider one built into a USB charger. No one would suspect it.
Building a Test Bug…
In our test, we didn’t try to be covert. We just slapped it on the back of a AAA battery pack. Furthermore, the bug was very small and could be easily hidden.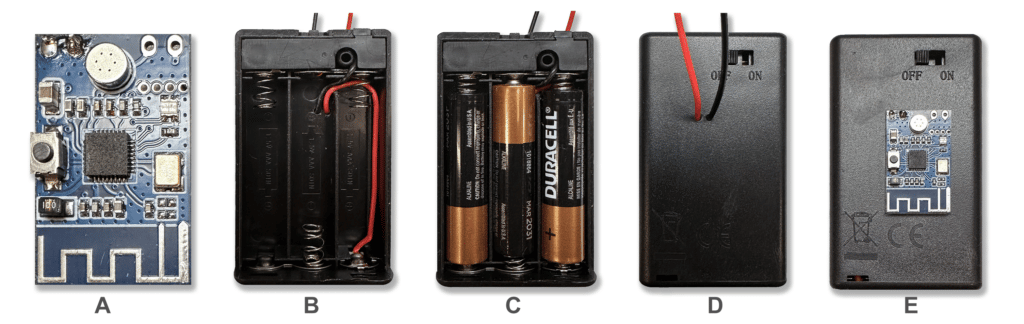
A – Enlarged View
B – Drill 2 Holes & Rewire
C – Add AAA Batteries
D – Front View
E – Solder & Affix Bug Transmitter
Pretty simple.
Test Results: When activated, the transmitter and receiver create their encrypted link automatically. The reception distance was as advertised. Adding a high-gain 2.4 GHz directional antenna on the receive end could boost this receive distance 3 to 4 times, thus making the bug an even more potent eavesdropping device. The most surprising results involved the clarity and sensitivity. The audio was crystal-clear, and any whispers in the area were picked up with ease.
TSCM Detection of the 2.4 GHz Bug
Detecting this bug was not easy. Several professional Technical Surveillance Countermeasures (TSCM) detection techniques were tried, but only one detection method succeeded reliably.
As a side note, if you are concerned about this type of attack you will need the help of a TSCM specialist to discover it, as none of the cheap bug detection gadgets would find this bug.
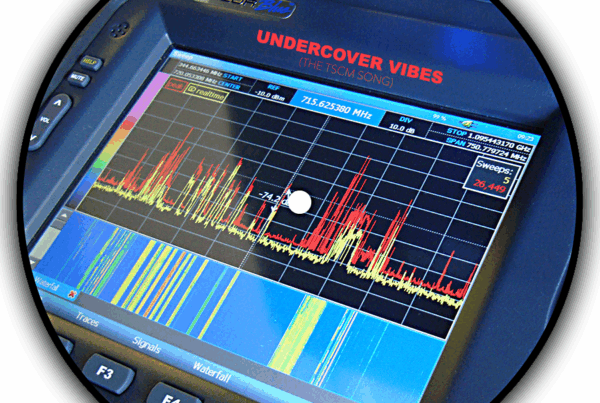
When the bug is transmitting, a distinctive spread-spectrum waveform can be shown using a Spectrum Analyzer, as seen in the video below. When the 2.4 GHz bug is active, it leaves a distinctive red shape resembling Bart Simpson’s haircut on the screen. When the bug is turned off, Wi-Fi and Bluetooth signals that were previously obscured by the bug transmission can be seen.
We invite you to learn more about Technical Surveillance Countermeasures (TSCM) services here. Or, contact us directly to engage our services.
###
Murray Associates is an independent security consulting firm, providing eavesdropping attack detection and counterespionage services to business, government, and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.
EXTRAS: • More security tips, spy and privacy news at spybusters.blogspot.com. Be sure to sign up for the free email updates. • Concerned about Spy Cameras? Learn how to detect them.