Introduction to Scheduled Office Building Bug Sweeps
![]() Office building bug sweeps to detect illegal listening devices are a common business practice. They counter corporate espionage and protect personal privacy.
Office building bug sweeps to detect illegal listening devices are a common business practice. They counter corporate espionage and protect personal privacy.
Also called TSCM (Technical Surveillance Countermeasures) inspections for corporations, they ensure critical information and data remains protected from even the most sophisticated unauthorized electronic surveillance techniques.
If you’re not already familiar with TSCM office building bug sweeps, or how to obtain them, here is an instant education.
“What is a TSCM inspection?”
A corporate TSCM inspection is a bug sweep detection service conducted by a trained team of counter-surveillance specialists. The aim is to detect spying or eavesdropping devices in office buildings, such as hidden cameras, microphones, and Wi-Fi vulnerabilities. Locations may also include: off-site meetings at hotels and conference centers, and modes of transportation such as automobiles, aircraft and yachts.
To perform this service, a TSCM technical team visits your organization to comprehensively inspect the most sensitive areas for unauthorized surveillance devices and recording equipment.
“Why should we schedule an office building bug sweep?”
Regularly scheduled TSCM inspections can help to keep your organization’s confidential data safe and private, all while preserving your company’s reputation. Electronic surveillance detection can help you avoid:
- Business Espionage
- Competitive Intelligence
- Mysterious Leaks
- Personal Privacy (including spycams in expectation of privacy areas)
- Malignant Activism
- Internal Intrigue
- Strategy Spying
- Media Snooping
- Blackmail
- Revenge
- Eavesdropping Concerns
- Adverse Publicity
“What do office bug sweep inspections protect?”
- Sensitive Communications
- Boardroom Discussions
- Mergers & Acquisitions
- Delicate Negotiations
- Lawsuit Strategies
- Employee Safety
- Trade Secrets
- Personal Privacy
- Vulnerable Off-site Meetings
- Wireless Local Area Networks (WLANS)
- Executive Residences & Home Offices
- Executive transportation (vehicles, aircraft)
Direct Benefits of Scheduled Office Building Bug Sweep Inspections
There are many reasons why you should consider regularly scheduled TSCM investigations, but the main benefits include:
- Increased profitability
- Intellectual property protection
- An environment secure from long-term electronic surveillance invasions
- Advance warning of intelligence collection activities (spying)
- Confirmation of the effectiveness of current security measures and practices
- Privacy law compliance
- Discovery of new information loopholes before they can be used against you
- Compliance with the legal requirement for “Business Secret” status in court
- Enhanced personal privacy and security
- Improved employee morale
- Wi-Fi security and privacy law compliance
- Increased employee respect for information security
- Increased effectiveness of established security measures
- Reduction of consequential losses, e.g. an information leak sparks a stockholder’s lawsuit, or…an activist releases of wiretaps to damage good-will and sales.
You can learn more about the benefits of corporate bug sweep detection services and enterprise best practices, here.
Benefits for Corporate Security Departments
Having a TSCM consulting firm conduct your office building bug sweeps provides you with substantial benefits.
- Zero capital investment for expensive instrumentation.
- There’s no need to attend expensive and time-consuming training schools, because these specialists will handle the technicalities for you.
- A TSCM consultant’s recommendations can fortify your own previous recommendations to management.
- There’s no risk to your own reputation if the TSCM bug sweep is not successful.
Important points:
- Periodic inspections are now a standard business practice across many sectors. Inspections are commonly performed quarterly or (less commonly) twice a year.
- Murray Associates’ scheduled office building bug sweeps inspections include an information security survey of the inspected areas, at no extra charge.
Office Building Bug Sweep Inspection Instrumentation
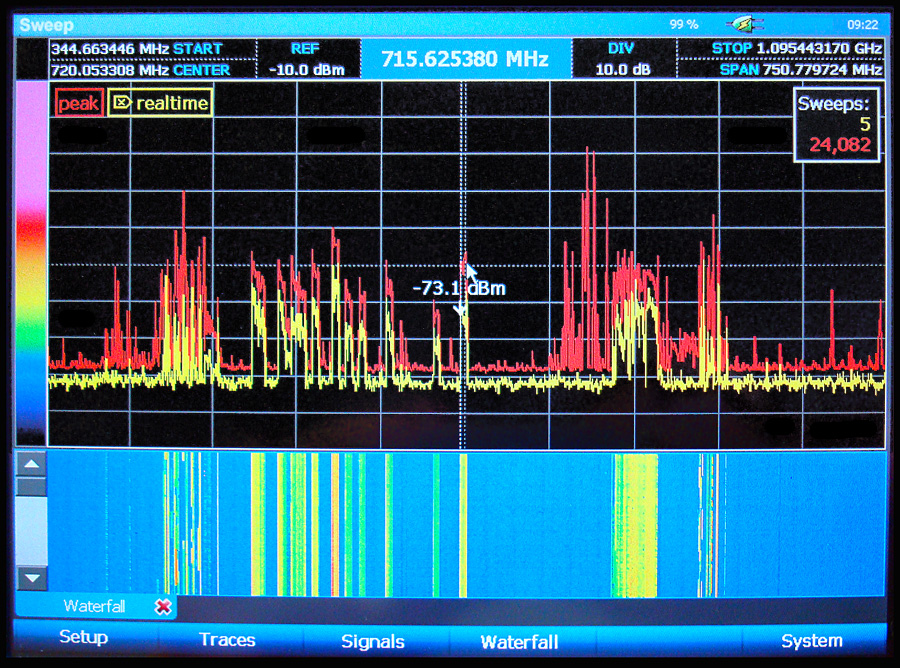
• Radio Reconnaissance Spectrum Analysis – A search for illegal surveillance devices which transmit (audio, video or data) information via radio waves.
• Thermal Emissions Spectrum Analysis – Detection of heat emitted by spycams, bugs and other electronic circuits. Heat signatures can be found even when the devices are hidden in ceiling tiles, walls, or furniture.
• Communications Systems Surveillance Analysis – a proprietary test method developed by Murray Associates – which identifies surveillance methods used to extract information from: telephones, faxes, computer networks, etc. In addition to inspecting the actual equipment (phones, speakerphones, faxes, video teleconferencing systems, etc.), wireless networks, LANs, and networked printers are also inspected. We also examine your wiring for taps and transmitters.
• Wi-Fi Security Audits with Compliance Analysis – This is an examination of how the wireless network security is configured. This is important because it only takes one loophole for hackers to get in and your data to get out. Lack of proper network security can also create compliance issues; fines are very expensive.
• Malicious USB Spy Cable Inspection – A malicious cable is any cable (electrical or optical) which performs an unexpected, and unwanted function. The most common malicious capabilities are found in USB cables. Data exfiltration, GPS tracking, and audio eavesdropping are the primary malicious functions.
• Mapped Physical Inspection – Areas are systematically mapped for physical inspection. Each area is combed with several objectives in mind: physical penetration evaluation of the premises; location of hidden surveillance devices; discovery of evidence indicating prior installations; alerting you to future surveillance possibilities; reporting on other security and safety issues encountered. This is the most important phase of the inspection, and relies heavily on security knowledge, experience, and intelligence. Example: A clear thread seen in a drape or carpet may look normal. Our technical investigators may suspect a fiber optic microphone… and search further.
• Non Linear Junction Detection – Areas are re-examined using non-destructive radar. This safe technique reveals semiconductor electronic components (transistors, diodes, etc.), the building blocks of electronic surveillance devices. Devices hidden in – or built into – furniture, ceiling tiles, and other objects can be identified with this technology… even if they are not active during the inspection!
“Will I receive a written report?”
Yes. Your written TSCM inspection report will detail: locations inspected, inspection results and security improvement recommendations, non-electronic information security vulnerabilities seen – with recommendations, and explanations of our inspection methodology and instrumentation. Photographs and an Inspection Log are usually included as well.
Your report is prepared by Kevin D. Murray, CPP, CISM, CFE, CDPSE, MPSC, an independent and credentialed security consultant with over four decades of experience. His report is proof of your due diligence.
Planning an Office Building Bug Sweep
Our planning booklet, The Security Director’s Guide to Planning an Effective TSCM Sweep, explains the whole process, but here are some quick tips:
- Plan a strategy.
- Define your security experience, concerns, and goals.
- Create a priority list of the locations requiring a detailed TSCM inspection. Even though some tests may cover the entire building, not every space requires a detailed inspection. Focusing attention on critical areas provides better results, and reduces costs.
- Determine the proper frequency of follow-up scheduled TSCM inspections — everyone’s window-of-vulnerability is different. Most organizations find quarterly or biannual inspections suit their needs. Some use a mixture of both.
- Schedule supplementary inspections, as required, for: off-site meetings, Board meetings, and situations where risks are elevated.
- Tell us about your organization’s concerns and goals. We can help with suggestions and strategy development. When contacting us, do so from “a safe location.”
“Do you need to visit my office building first?”
It is very rarely necessary to inconvenience you – or tip our hand – with a preliminary visit. If you think we need to see something specific, a mobile phone Zoom call may be all that is needed.
“Could you give me just a rough idea of the cost?”
This depends upon the size and complexity of the assignment. Executive suite areas (5-10 offices) are averaging between $7,000 – $12,000. Scheduled re-inspections are less. Travel expenses are only charged as incurred, and are estimated in advance for you.
“May I call you with additional questions?”
Of course, please call us with your questions (800-635-0811 or +1-908-832-7900). We are here to help you.
The Next Step – Request a TSCM Proposal
Complete our one-page TSCM assignment details sheet located in our Introductory Booklet, or on-line. Include a floor map which indicates the sensitive areas requiring the office building bug sweep inspection. Tip: Create a priority list of sensitive areas requiring inspection. Remember, not every square foot will require a detailed inspection. The radio-frequency portion of our inspections will cover large areas surrounding your sensitive areas by default, at no extra charge.
We will send you an accurate, no-obligation, written proposal – estimated expenses included. Sign-off and return a copy to us. We can then decide upon a mutually convenient inspection schedule.
If you have any questions not answered here, please contact us, or ask our AI Site Search in the lower right-hand corner.
Upon Acceptance of the Office Building Bug Sweep Proposal
Together, we arrange a mutually convenient time to conduct your inspection. Our services are available any time, any day or night. We handle all the travel arrangements. Simply pick a time and date and we will be there.
Upon arrival, we will review your goals and learn about any late-breaking events, and take a brief orientation tour of your facility before beginning the TSCM inspection.
Each inspection unfolds differently. Information (visual, audio and data) can be transferred from sensitive areas in a variety of ways. There is no “one” test, technique, or gadget which will detect every method. Our custom protocols and specialized instrumentation are selected to fit your specific security situation.
If your concerns are an emergency please collect as much incident background information as you can for us, and…
- Do not discuss our services in, or call from suspect areas.
- Conduct your affairs normally.
- Do not reveal any suspicions you may have to others.
- Limit confidential conversations.
- Keep detailed notes about anything you feel is suspicious.
- Think ahead. If a device is found, what next? We can advise you on this.
It is crucial you don’t give any malicious insiders reason you suspect them. Otherwise, surveillance devices could be removed before the investigation.
- Scheduled TSCM inspections are not intrusive.
- Inspections may be scheduled at your convenience.
- You specify the areas to inspect and/or not to inspect.
- Inspection of vehicles may also be conducted at the same time.
Most importantly, we fully respect your privacy and confidentiality.
Have a Question About TSCM?
If you have any questions about the TSCM assessments provided by Murray Associates consultants, download our brochure, drop us a note, or call us from a safe area and phone.
If you think you are under active electronic surveillance, or believe you have discovered a bug or covert video camera, follow the directions above and visit our post “I think I found a bug. What do I do?” The procedural checklist there will also tell you exactly what you need to do next.
