 Not for sale to the general public.
Not for sale to the general public.
Available as a consulting supplement for our clients. Limited-time offer.
A licensing opportunity is available. Contact us.
SpyWarn Anti-Spyware Kit for Smartphones
A unique security protocol to increase privacy.
It also makes a thoughtful and welcome gift.
Instructions
1. SPYWARN MicSpike™
Your phone cannot be used for remote eavesdropping when the microphone is disabled. Plug the MicSpike into the headphone jack when you require privacy. The phone senses the plug’s electronics and is tricked into believing the MicSpike™ is an external microphone. The internal microphone remains unusable until you remove the MicSpike.
Use the SpyWarn MicSpike in these situations too:
- At confidential business meetings, have meeting participants plug the MicSpike into their mobile phones during meetings. The SpyWarn MicSpike will allow them to receive and respond to important emails and text messages, but doing this is not recommended during confidential meetings.
- In high security areas, where photos, recordings, and phone calls are not allowed, security or reception can place a seal over the visitor’s phone camera lens. A second seal is used to secure the MicSpike™ plug in the earphone jack. The serial numbers are recorded. When the visitor departs the area, the seal integrity is checked, and the MicSpike plug is retrieved.


SpyWarn MicSpikes come individually or in sets of 25 for boardroom/conference room use.
2. SPYWARN THERMAL SENSOR™

When your phone is transmitting or recharging, it warms up. This is normal. However, if your phone warms up when you are not using it, suspect it has been activated by spyware, remote baseband hacking, or a denial-of-service Silent SMS attack.
The sensor adheres to the back of the phone. The three indicators turn slowly from black to red, one by one, as the phone’s temperature rises.
Some phones may only illuminate the first indicator. Other phones may illuminate all three. Any unexpected rise in temperature is suspicious.
NOTES:
- The SpyWarn Thermal Sensor™ is used under very controlled conditions – when the phone is at room temperature (68º-74º F / 20º-23.3º C). Its detection capability declines when the ambient temperature is outside of this range.
- If the phone has been used recently, or was in your pocket, it may take a while for it to reach room temperature.
- A change in any indicator’s brightness (especially a 50% increase) is meaningful, assuming the ambient temperature is stable.
- Due to the variety of materials used in phones, the transfer of heat to the sensor varies. Metals transfer heat faster than plastics, for example. Sensor response time will always lag real time events. Temperature may continue to rise even after a transmission ends. The important point is that a rise in temperature was sensed while you were not using the phone.
- The sensor is sensitive to the sun’s harmful ultra-violet rays. Avoiding bright sunlight will extend the sensor’s lifespan.
Most phones heat up unevenly across their surfaces. Exact spots and temperature vary with different models. Before permanently attaching the sensor, conduct a few tests to determine the best location for placement.
Tip: We can check your phone with our thermal imaging camera to find the best spot during our next Technical Surveillance Countermeasures (TSCM) visit with you.
A. Make sure the phone is at or near room temperature, turned on, and ready to receive a call. Place it face down on a table.
B. Lay the SpyWarn Thermal Sensor™ flat on the back of the phone; on top of the battery is usually a good spot. You may want to temporarily tape down so that it makes good contact. Wait a minute. If the sensor illuminates you may be over a naturally warm circuit board. Move the sensor to a new location and wait for the red to disappear.
C. Make a call between your phone and another phone. Keep the connection open. Place your phone on the table, face down, with the thermal sensor laying flat on the back. As your phone warms, you should see the first indicator slowly turn red. If so, this is a good location for the sensor. If not, try another spot.
D. When you are satisfied the sensor is properly placed, permanently attach it to the rear of your phone.
General Usage
When you are not using your phone, leave it nearby, face down, and occasionally look at the strip. If you notice the red indicators have increased in number and/or brightness, it is likely your phone has been activated.
Additional SpyWarn Thermal Sensors™ are available individually to our clients, at cost.
3. SPYWARN SECURITY SEAL™

SpyWarn Security Seals™ prevent secret removal of your SIM and SD memory cards for snooping or planting of spyware programs.

Phone SIM and SD memory cards contain a wealth of information: contacts, calls made, recent SMS text messages, photos, music, emails, etc. SD memory cards can also store apps, including spyware apps.
Unprotected, these cards may be secretly removed from your phone and read from, or written to using an inexpensive SIM or SD memory card reader.
How would you know if someone removed your SIM or SD cards, even if only for a few minutes?
Easy. Place a SpyWarn Security Seal™ over them.
The SpyWarn Anti-Spyware Kit for Smartphones™ contains two one-time-use high security seals and two wipe pads.
- Clean the phone’s surface with a wipe pad, removing all grease and dirt. The seals require a clean surface for proper adhesion.
- Peel off the seal’s backing and apply it very carefully. Try not to touch the adhesive. Do not try to reposition the seal.
A wipe pad may also be used to remove adhesive residue should you want to remove a seal or thermal sensor later.
Tip: Do not try to affix any part of the seal to your phone’s glass screen, as it will not stick. On iPhones, line up the top of the seal with the FLAT edge of the bezel. Fold the seal over to the back of the phone (as seen in the picture above).
Our seals have a semi-transparent hologram embedded in them for extra security. For super security and privacy, invisible ink is used for the lettering. Lettering only appears when illuminated with a UV black light. Each seal has its own unique serial number.
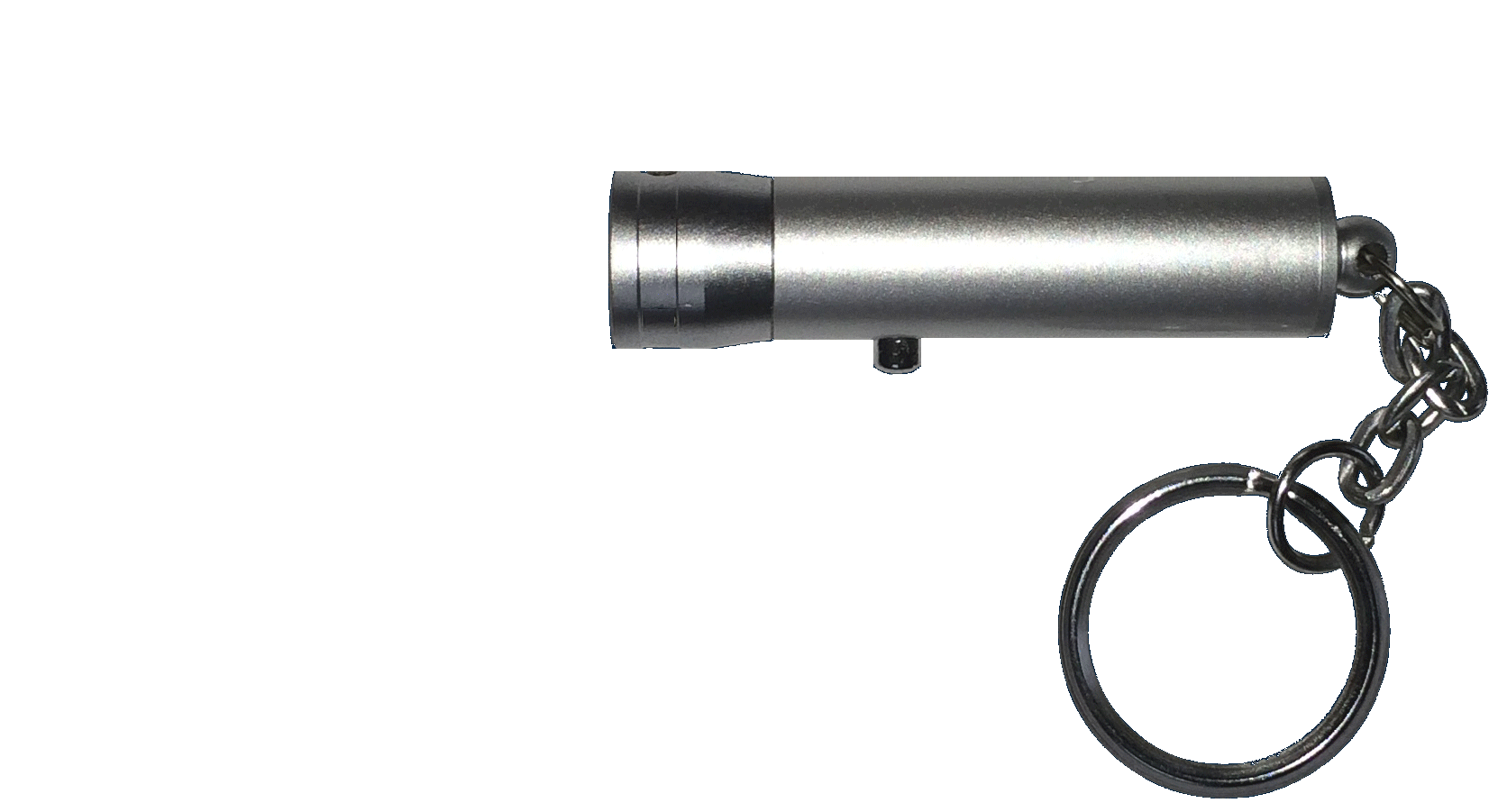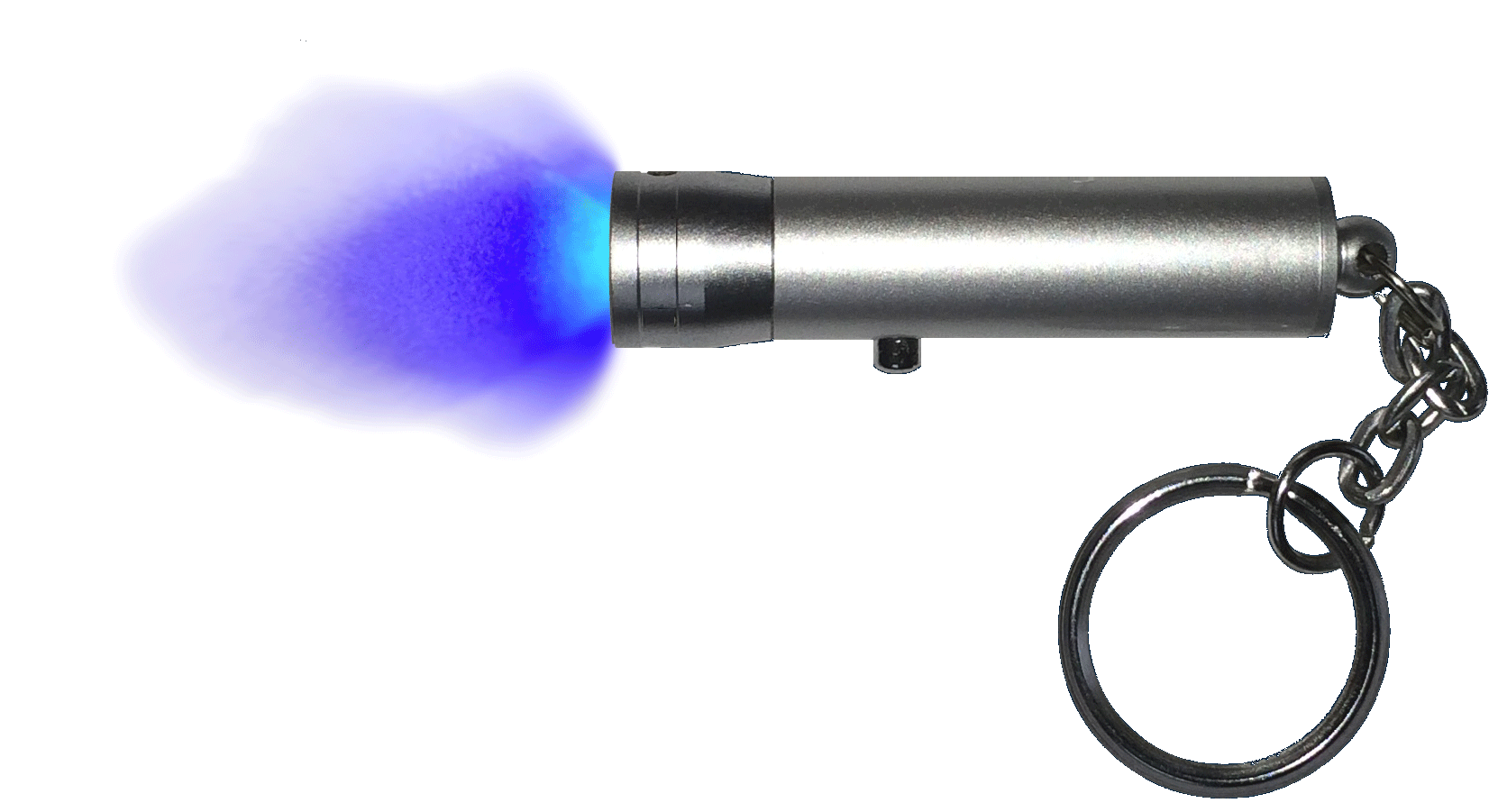
If someone tries to remove the seal, it will self-destruct and cannot be put back in place again.
Place the seals over your SIM card slot ensuring the surface is grease-free and otherwise clean. If your phone has an SD memory card, place a seal over it as well. The seals may be trimmed to size.
If you notice a seal is missing or appears damaged you will know someone has violated your phone.
Simply having your cards sealed puts any potential snoops on notice that you are watching. This acts as a powerful deterrent against tampering.
SpyWarn Security Seals may be used to seal other smooth surfaced items, too…
- Diaries
- Safes
- Keyways
- Liquor and Gun Cabinets
- Office and Hotel Room Doors
- Equipment Cabinets
- Desk Phones
- Envelopes
- Desks, Filing Cabinets
- Plastic boxes holding emergency keys
- Computers and Laptops – deter and detect…
– Lid lifting
– Case opening,
– Camera use,
— or insertion of unauthorized USB devices and CDs.
Use SpyWarn Security Seals™ in extremely high-security locations.
When photos, recordings and phone calls are not allowed, a security officer or receptionist places a seal over the camera lens on the visitor’s phone. A second seal is used to secure a SpyWarn Microphone Disabler™ plug in the earphone jack. The serial numbers are recorded.
When the visitor departs the area, the seal integrity is checked, and the SpyWarn Microphone Disabler™ plug is retrieved.
Additional SpyWarn Security Seals, Wipe Pads and Mini UV Black Lights for reading serial numbers are available individually to our clients, at cost.
SPYWARN™ Book & App
(FREE to Murray Associates clients)
Everything you need to know to keep your communications private.
• SpyWarn™ 2.0 (Android app) (FREE to clients)
 A new forensic app for evaluating the presence of spyware on Android smartphones. Learn more at SpyWarn.com or Google Play.
A new forensic app for evaluating the presence of spyware on Android smartphones. Learn more at SpyWarn.com or Google Play.
“The antivirus industry has a dirty little secret: its products are often not very good at stopping viruses.” – The New York Times
Common anti-spyware apps are ineffective. They only look for known viruses; new and well-hidden spyware often goes unnoticed.
SpyWarn™ 2.0 is different. It spots infections by detecting what the spyware is doing.
And all spyware is doing something. SpyWarn™ 2.0 also detects remote baseband eavesdropping, something no other anti-spyware app even tries to do.

